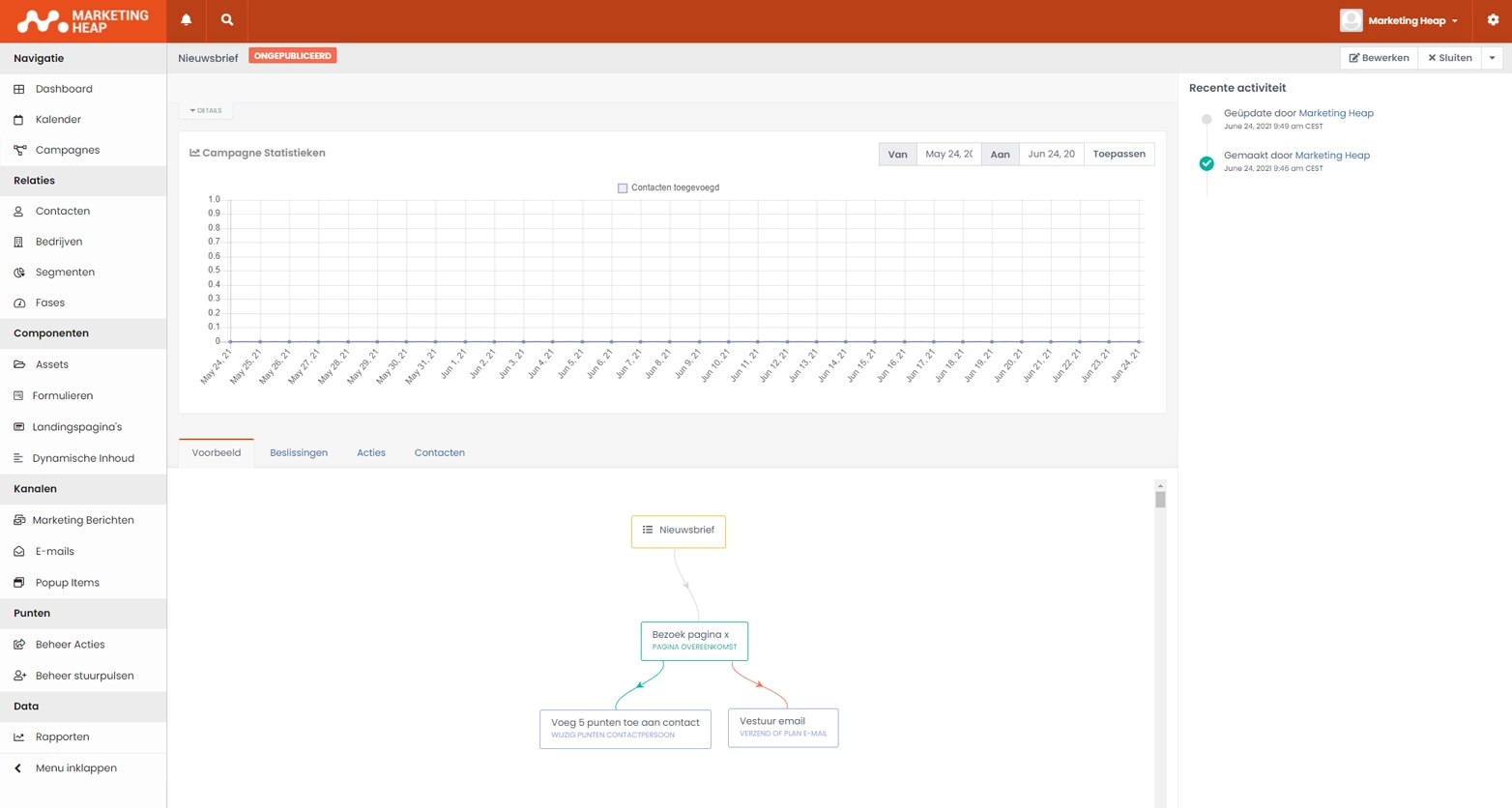
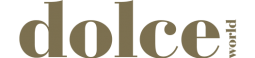Wat is MarketingHeap?
MarketingHeap is een unieke marketing automation-oplossing. Waarom? Het is een open source platform. Dit betekent dat de marketing automation-software die Marketingheap biedt continu wordt ontwikkeld door honderden individuele ontwikkelaars. Met hun ideeën en skills dragen zij bij aan het optimaliseren van de software, waardoor het platform constant wordt verrijkt met nieuwe functionaliteiten die zijn gebaseerd op de vragen uit de markt.
MarketingHeap is veel betaalbaarder dan andere marketing omgevingen.
Begin nuErvaar het zelf!Begin nu
Bij het registreren krijg je 30 dagen volledige toegang tot alle features van de MarketingHeap omgeving
Waarom kiezen voor MarketingHeap?
MarketingHeap biedt alle belangrijke features die je nodig hebt van marketing automation. Van een gebruiksvriendelijk management dashboard tot de optie om het platform helemaal naar jouw wensen in te richten.
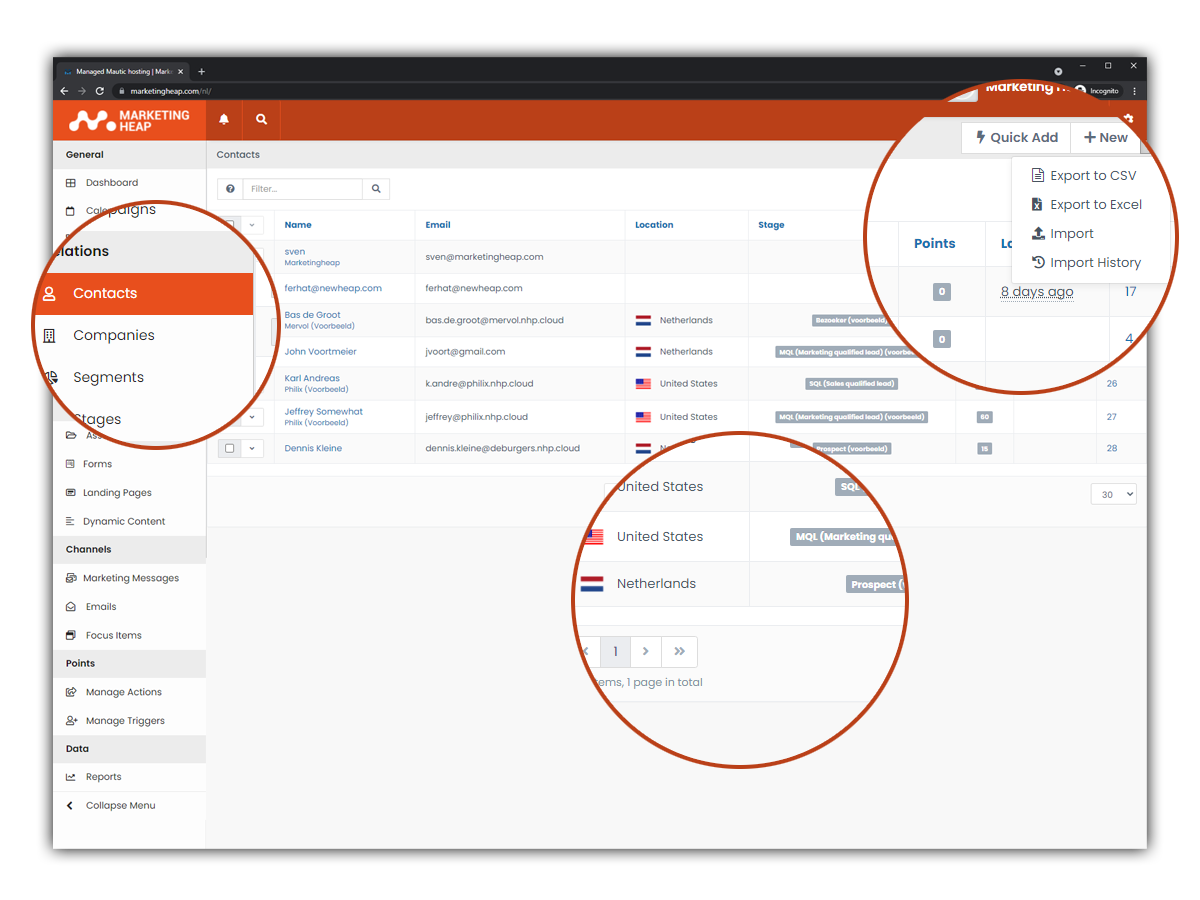
Waarom MarketingHeap Automation
Waarom zou je kiezen MarketingHeap Automation? Allereerst wil je als organisatie dat jouw marketing automation draait op een betrouwbaar platform. Daarnaast heb je ook een partner nodig die jou ondersteunt bij de start en helpt met het verder ontwikkelen van jouw marketing automation. MarketingHeap Automation heeft een marketing automation platform ontwikkeld, gebaseerd op Mautic, waar iedereen op een betaalbare manier kan beginnen met digitale marketing. Wij bieden de MarketingHeap-oplossing aan, hosten het en bieden jou de nodige ondersteuning. Daarnaast zorgen we ervoor dat het platform veilig en betrouwbaar is. We hebben tenslotte te maken met persoonlijke klantdata.